SSH as service - more use cases
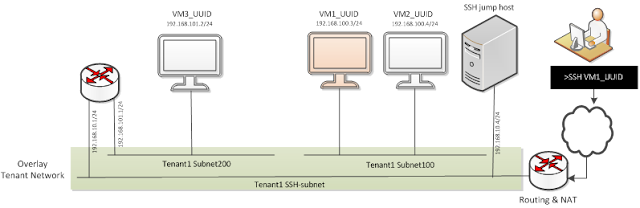
In previous post I described the most straightforward use case of SSH service usage: access VM at routable tenant private network. The more interesting case could be to access a VM1_UUID that lays on not routable network: Tenant1 Subnet100 figure 1 Achieving SSH connectivity requires SSH gate (SSH jump host) to have a network interface on Tenant1 Subnet100. SSH service have to allocate neutron port on Tenant1 Subnet100 network and attach new port to SSH gate. Dynamic port attachment requires some underground SSH gate network configuration. SSH Service daemon can access SSH gate VM with SSH management key and update network configuration. figure 2 Now traffic may flow to VM1_UUID even without router involvement. Authentication is performed gradually. We may use same concept of SSH configuration file with proxy command. figure 3 Generic SSH service Both routable and no routeable VM connection schemes lays on boundary of specific tenant. The more gen...


